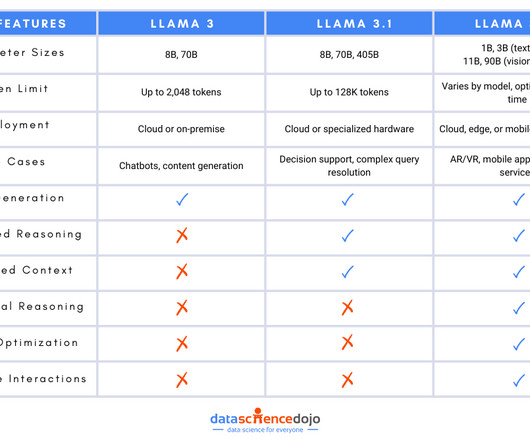
Comparing the Llama Models: Llama 3 vs Llama 3.1 vs Llama 3.2
Data Science Dojo
NOVEMBER 8, 2024
Key Updates Enhanced text generation capabilities Improved contextual understanding Better logical reasoning Purpose: The launch aimed to cater to the growing demand for sophisticated AI that could engage in more meaningful and contextually aware conversations, improving user interactions across various platforms. Second Iteration: Llama 3.1














































Let's personalize your content