Collection of Free Courses to Learn Data Science, Data Engineering, Machine Learning, MLOps, and LLMOps
KDnuggets
FEBRUARY 28, 2024
Begin your data professional journey from the basics of statistics to building a production-grade AI application.

KDnuggets
FEBRUARY 28, 2024
Begin your data professional journey from the basics of statistics to building a production-grade AI application.

Hacker News
FEBRUARY 14, 2024
We terminated accounts associated with state-affiliated threat actors. Our findings show our models offer only limited, incremental capabilities for malicious cybersecurity tasks.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
BAIR
FEBRUARY 17, 2024
These are comments in HTML. The above header text is needed to format the title, authors, etc. The "example_post" is an example representative image (not GIF) that we use for each post for tweeting (see below as well) and for the emails to subscribers. Please provide this image (and any other images and GIFs) in the blog to the BAIR Blog editors directly.
Hacker News
FEBRUARY 29, 2024
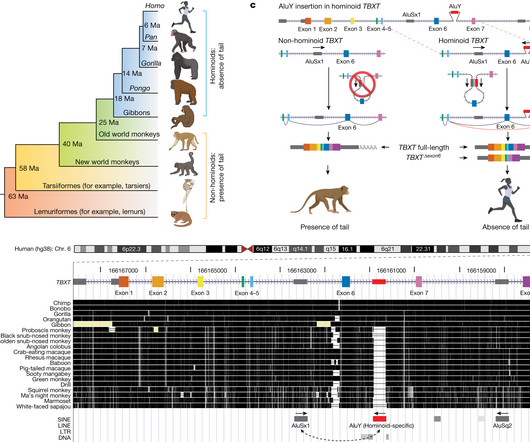
The loss of the tail is among the most notable anatomical changes to have occurred along the evolutionary lineage leading to humans and to the ‘anthropomorphous apes’1–3, with a proposed role in contributing to human bipedalism4–6. Yet, the genetic mechanism that facilitated tail-loss evolution in hominoids remains unknown. Here we present evidence that an individual insertion of an Alu element in the genome of the hominoid ancestor may have contributed to tail-loss evolu

Speaker: Conrado Morlan
In this engaging and witty talk, we’ll explore how artificial intelligence can transform the daily tasks of product managers into streamlined, efficient processes. Using the lens of a superhero narrative, we’ll uncover how AI can be the ultimate sidekick, aiding in decision-making, enhancing productivity, and boosting innovation. Attendees will leave with practical tools and actionable insights, motivated to embrace AI and leverage its potential in their work. 🦸 🏢 Key objectives:
Hacker News
FEBRUARY 29, 2024
As California prepares to implement a new law that requires major fast food chains to pay workers a minimum of $20 an hour starting in April, a new report explains why the governor's relationship with a billionaire helped exempt Panera Bread and chain restaurants like it.

Hacker News
FEBRUARY 29, 2024
I'm unsure how popular GameNOW magazine was, but over the course of two years, they pulled off one of the weirdest running gags I've seen in a game magazine, just to have fun at the expense of an irate reader who didn't like Final Fantasy VIII.
Data Science Current brings together the best content for data science professionals from the widest variety of thought leaders.
Hacker News
FEBRUARY 28, 2024
Malicious hackers are targeting people in the cryptocurrency space in attacks that start with a link added to the target’s calendar at Calendly , a popular application for scheduling appointments and meetings. The attackers impersonate established cryptocurrency investors and ask to schedule a video conference call. But clicking the meeting link provided by the scammers prompts the user to run a script that quietly installs malware on macOS systems.

Hacker News
FEBRUARY 16, 2024
Showmax sits at the top of the market with a vast library of local content, partnerships with Comcast and HBO, and exclusive access to the biggest football leagues in the world.

Hacker News
FEBRUARY 27, 2024
The US used artificial intelligence to identify targets hit by air strikes in the Middle East this month, a defense official said, revealing growing military use of the technology for combat.

Hacker News
FEBRUARY 27, 2024
Apple Inc. is canceling a decadelong effort to build an electric car, according to people with knowledge of the matter, abandoning one of the most ambitious projects in the history of the company.

Advertisement
The complexity of financial data, the need for real-time insight, and the demand for user-friendly visualizations can seem daunting when it comes to analytics - but there is an easier way. With Logi Symphony, we aim to turn these challenges into opportunities. Our platform empowers you to seamlessly integrate advanced data analytics, generative AI, data visualization, and pixel-perfect reporting into your applications, transforming raw data into actionable insights.

Hacker News
FEBRUARY 27, 2024
Google launched a private program for a handful of independent publishers last month, providing the news organizations with beta access to an unreleased generative artificial intelligence platform in exchange for receiving analytics and feedback, according to documents seen by ADWEEK. As part of the agreement, the publishers are expected to use the suite of tools.

Hacker News
FEBRUARY 27, 2024
Farmers in hot, arid regions are turning to low-cost solar pumps to irrigate their fields, eliminating the need for expensive fossil fuels and boosting crop production. But by allowing them to pump throughout the day, the new technology is drying up aquifers around the globe.

Hacker News
FEBRUARY 27, 2024
Testcontainers is an opensource framework for providing lightweight, throwaway instances of common databases, Selenium web browsers, or anything else that can run in a Docker container.

Hacker News
FEBRUARY 25, 2024
Workers sent from the country to Chinese factories describe enduring beatings and sexual abuse, having their wages taken by the state, and being told that if they try to escape they will be “killed without a trace.

Advertisement
Adding high-quality entity resolution capabilities to enterprise applications, services, data fabrics or data pipelines can be daunting and expensive. Organizations often invest millions of dollars and years of effort to achieve subpar results. This guide will walk you through the requirements and challenges of implementing entity resolution. By the end, you'll understand what to look for, the most common mistakes and pitfalls to avoid, and your options.

Hacker News
FEBRUARY 26, 2024
Expedia Group Inc. is eliminating about 9% of its workforce after announcing a leadership transition earlier this month while the online travel company attempts to revive growth and regain market share.

Hacker News
FEBRUARY 29, 2024
More than 1 billion people — or one in eight people worldwide — are now estimated to have obesity, a new study finds. Obesity rates grew particularly fast among children and teens, quadrupling from 1990 to 2022, the latest year the analysis looked at, while rates among adults more than doubled. That comes to 159 million children and teens with obesity, and 879 million adults, according to the study, published Thursday in the Lancet and conducted by the NCD Risk Factor Collaboration

Hacker News
FEBRUARY 24, 2024
Today, the Department of Commerce’s National Telecommunications and Information Administration (NTIA) launched a Request for Comment on the risks, benefits and potential policy related to advanced artificial intelligence (AI) models with widely available model weights – the core component of AI systems.

Hacker News
FEBRUARY 12, 2024
Tesla Inc. sold just one electric vehicle in South Korea in January as a raft of headwinds, from safety concerns to price and a lack of charging infrastructure, weigh on demand.

Speaker: Ketan Jahagirdar
Picture your projects as patients, each with its own unique rhythm and pulse, thriving under your care 🥼 🩺 Step into the role of an innovative project doctor in our upcoming webinar! This session is your guide to evaluating the health of your projects through Waterfall and Agile practices like Scrum and Kanban. We’ll explore the vital signs of project success through the lens of the “iron triangle” metrics, using deliverables as tracers.
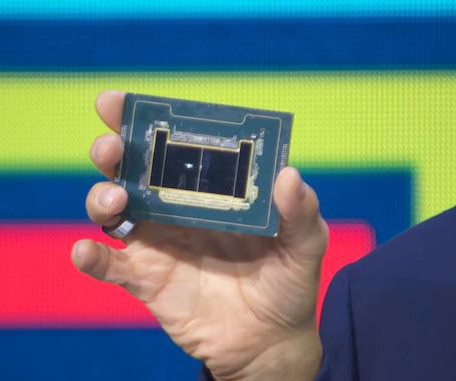
Hacker News
FEBRUARY 26, 2024
At MWC 2024, Intel confirmed that Granite Rapids-D, the successor to Ice Lake-D processors, will come to market sometime in 2025. Furthermore, Intel also provided an update on the 6th Gen Xeon Family, codenamed Sierra Forest, which is set to launch later this year and will feature up to 288 cores designed for vRAN network operators to improve performance in boost per rack for 5G workloads.

Hacker News
FEBRUARY 23, 2024
Nach langer politischer Auseinandersetzung hat der Bundestag am Freitag, 23. Februar, den kontrollierten Umgang mit Cannabis gebilligt. Mit dem Gesetz soll Erwachsenen künftig der Besitz von bis zu 50 Gramm Cannabis für den Eigenkonsum im privaten Raum erlaubt werden. Im öffentlichen Raum soll die Höchstgrenze bei 25 Gramm liegen. In namentlicher Abstimmung votierten 407 Abgeordnete für das Gesetz, 226 stimmten dagegen und vier enthielten sich.

Hacker News
FEBRUARY 23, 2024
Welcome! The fact that you’re reading this means that you probably care deeply about the issue of privacy, which warms our hearts. Unfortunately, even though you care about privacy, or perhaps because you care so much about it, you may feel that there's not much you (or anyone) can really do to.
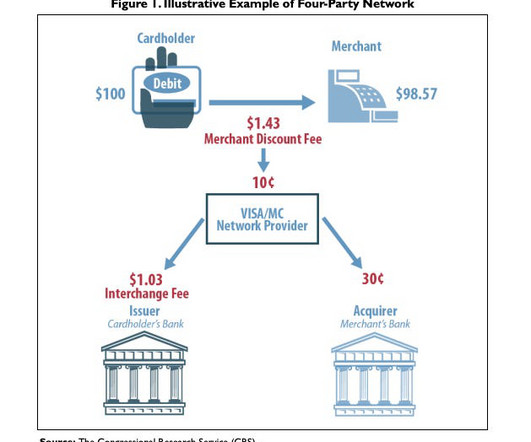
Hacker News
FEBRUARY 22, 2024
In 2010, Congress capped fees for debit card networks so merchants don't get gouged by Visa and Mastercard. But the Fed stuck in a loophole for Discover. And that is leading Capital One to buy it.

Speaker: Maher Hanafi, VP of Engineering at Betterworks & Tony Karrer, CTO at Aggregage
Executive leaders and board members are pushing their teams to adopt Generative AI to gain a competitive edge, save money, and otherwise take advantage of the promise of this new era of artificial intelligence. There's no question that it is challenging to figure out where to focus and how to advance when it’s a new field that is evolving everyday. 💡 This new webinar featuring Maher Hanafi, VP of Engineering at Betterworks, will explore a practical framework to transform Generative AI pr
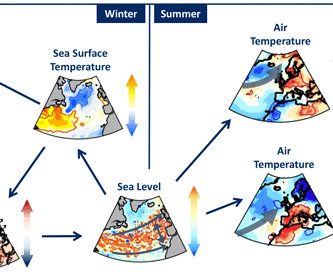
Hacker News
FEBRUARY 27, 2024
Abstract. Amplified Arctic ice loss in recent decades has been linked to the increased occurrence of extreme mid-latitude weather. The underlying mechanisms remain elusive, however. One potential link occurs through the ocean as the loss of sea ice and glacial ice leads to increased freshwater fluxes into the ocean. Thus, in this study, we examine the link between North Atlantic freshwater anomalies and European summer weather.

Hacker News
FEBRUARY 24, 2024
The Korean telecommunications watchdog said Friday it has slapped a fine of 435 million won ($327,067) on the U.S. live video streaming platform Twitch, which suspended its video-on-demand (VOD) service in the country last year.

Hacker News
FEBRUARY 22, 2024
Announcing Stable Diffusion 3 in early preview, our most capable text-to-image model with greatly improved performance in multi-subject prompts, image quality, and spelling abilities.

Hacker News
FEBRUARY 21, 2024
BYD has launched its low cost sedan in China which industry observers are calling the Corolla Killer. The post “Corolla killer:” BYD launches $US15,000 EV in direct attack on legacy makers appeared first on The Driven.

Speaker: Timothy Chan, PhD., Head of Data Science
Are you ready to move beyond the basics and take a deep dive into the cutting-edge techniques that are reshaping the landscape of experimentation? 🌐 From Sequential Testing to Multi-Armed Bandits, Switchback Experiments to Stratified Sampling, Timothy Chan, Data Science Lead, is here to unravel the mysteries of these powerful methodologies that are revolutionizing how we approach testing.

Hacker News
FEBRUARY 21, 2024
Nielsen today released its January report on viewing usage across linear TV and streaming, which revealed that YouTube is once again the overall top streaming service in the U.S., with 8.6% of viewing on television screens. Netflix, meanwhile, saw 7.9% of TV usage.
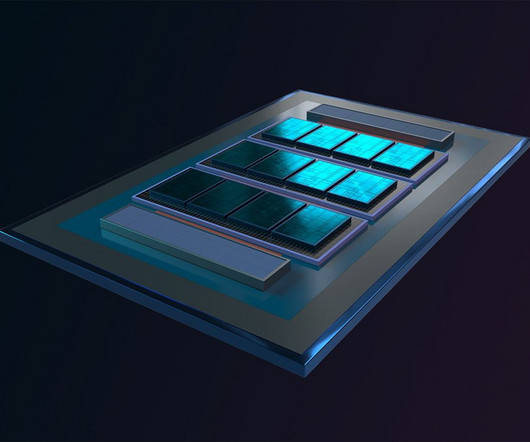
Hacker News
FEBRUARY 21, 2024
In an exclusive interview ahead of an invite-only event today in San Jose, Intel outlined new chip technologies it will offer its foundry customers by sharing a glimpse into its future data-center processors. The advances include more dense logic and a 16-fold increase in the connectivity within 3D-stacked chips, and they will be among the first top-end technologies the company has ever shared with chip architects from other companies.

Hacker News
FEBRUARY 20, 2024
The authors of the dangerous Kids Online Safety Act (KOSA) unveiled an amended version this week, but it’s still an unconstitutional censorship bill that continues to empower state officials to target services and online content they do not like.
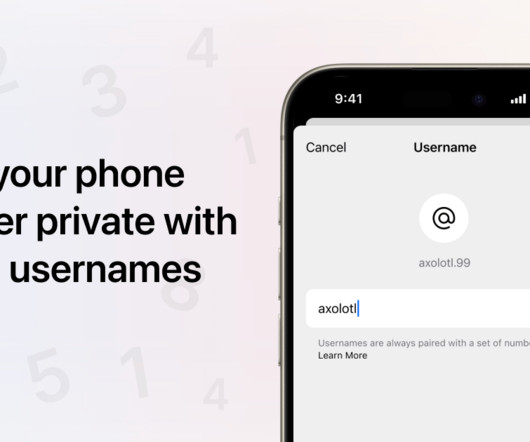
Hacker News
FEBRUARY 20, 2024
Signal’s mission and sole focus is private communication. For years, Signal has kept your messages private, your profile information (like your name and profile photo) private, your contacts private, and your groups private – among much else. Now we’re taking that one step further, by making your.

Speaker: Pulkit Agrawal
Digital Adoption Platforms (DAPs) are revolutionizing the way organizations interact with and optimize their software applications. As digital transformation continues to accelerate, DAPs have become essential tools for enhancing user engagement and software efficiency. This session is your guide into the robust world of DAPs, exploring their origins, evolution, and the current trends shaping their development.
Let's personalize your content