AI in Cybersecurity: Revolutionizing threat detection and defense
Data Science Dojo
AUGUST 2, 2023
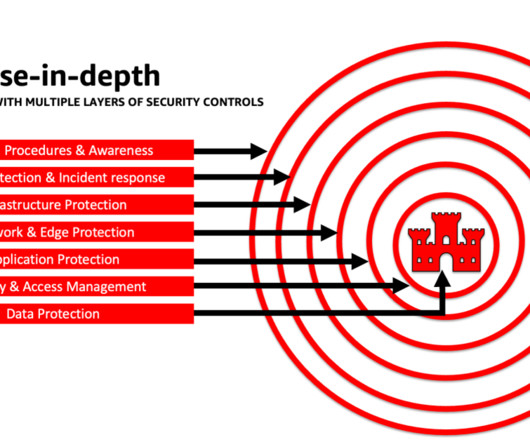
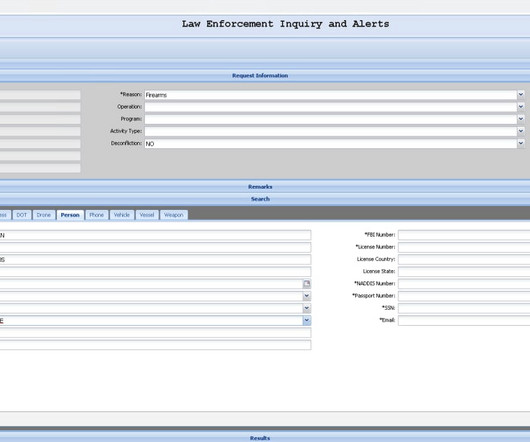
Can AI in cybersecurity help defend against evolving threats? The need to safeguard networks, systems, and data from diverse threats, such as malware, phishing, and ransomware, has never been more urgent. Behavioral Analysis and User Monitoring: AI detects suspicious user activities, protecting against insider threats.













































Let's personalize your content