Creating a web app for Gradio application on Azure using Docker: A step-by-step guide
Data Science Dojo
FEBRUARY 22, 2023
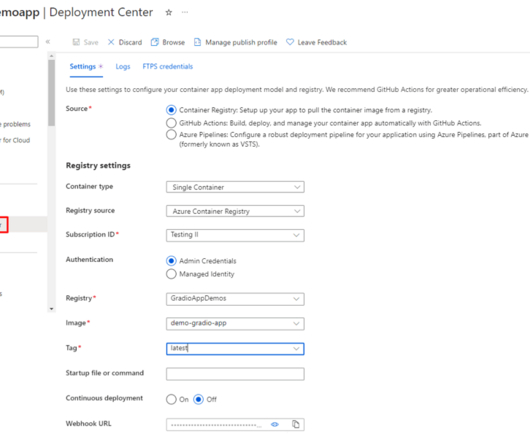
It allows you to store, manage, and deploy Docker containers in a secure and scalable way, making it an important tool for modern application development and deployment. ACR also provides features such as image signing and scanning, which helps ensure the security and compliance of your containers.






































Let's personalize your content