Best practices for building secure applications with Amazon Transcribe
AWS Machine Learning Blog
MARCH 25, 2024
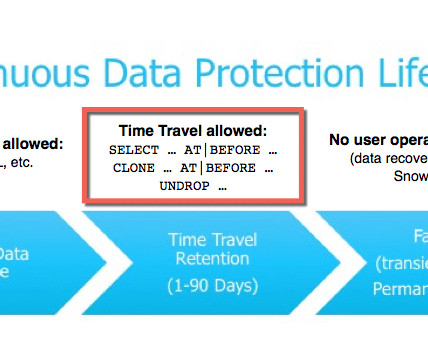
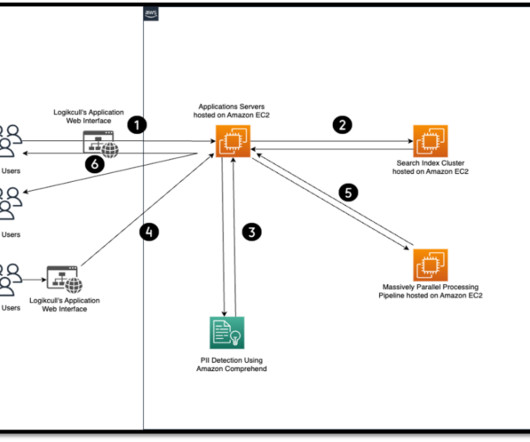
Protecting data in transit Data encryption is used to make sure that data communication between your application and Amazon Transcribe remains confidential. TLS provides authentication and encryption of data in transit using AWS certificates. In this case, the same SSE-S3 and SSE-KMS encryption options apply.


































Let's personalize your content