Unlock personalized experiences powered by AI using Amazon Personalize and Amazon OpenSearch Service
AWS Machine Learning Blog
FEBRUARY 29, 2024
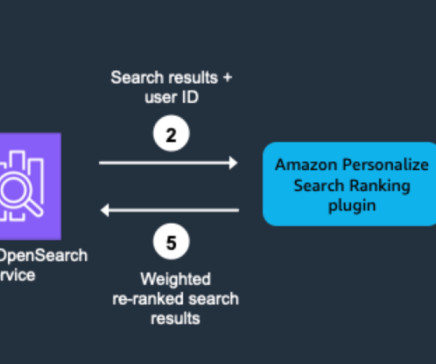
tag No None Specify an identifier for the processor. The closer to 1.0 that it is, the more likely it is that results from Amazon Personalize rank higher. If you specify 0.0, no personalization occurs and OpenSearch Service takes precedence. iam_role_arn Yes None Specify the IAM role to access Amazon Personalize resources. es.amazonaws.com.











Let's personalize your content