AutoDev: Automated AI-driven development by Microsoft
Hacker News
MARCH 16, 2024
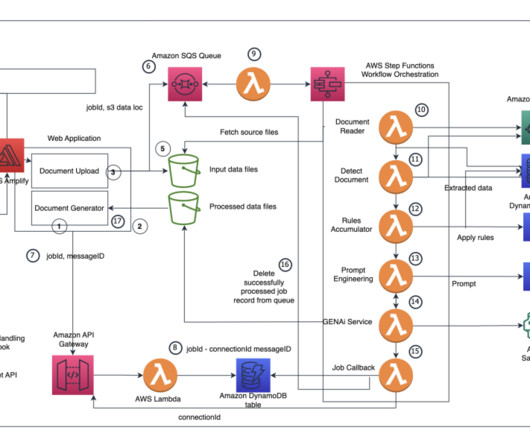
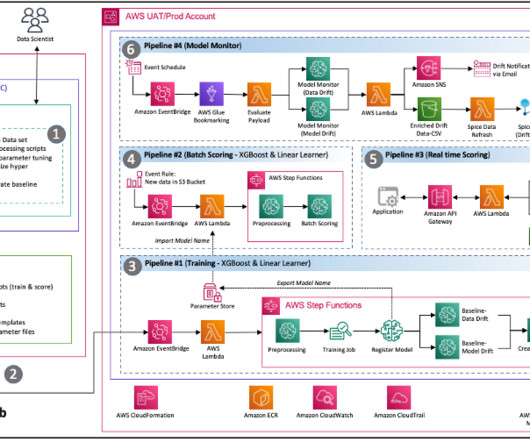
However, existing solutions are not leveraging all the potential capabilities available in an IDE such as building, testing, executing code, git operations, etc. These AI agents can perform diverse operations on a codebase, including file editing, retrieval, build processes, execution, testing, and git operations.











































Let's personalize your content