How To Use Dynamic Data Masking for Virtual Columns in Snowflake External Tables
phData
OCTOBER 23, 2023
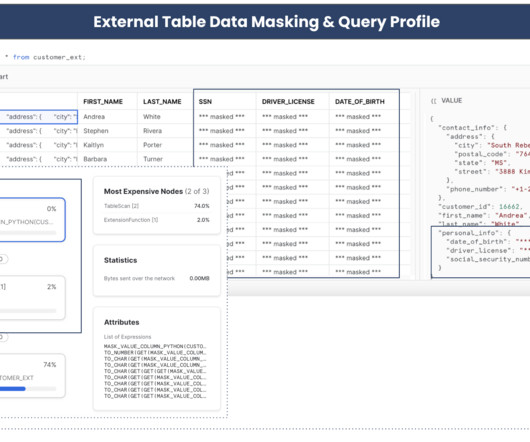
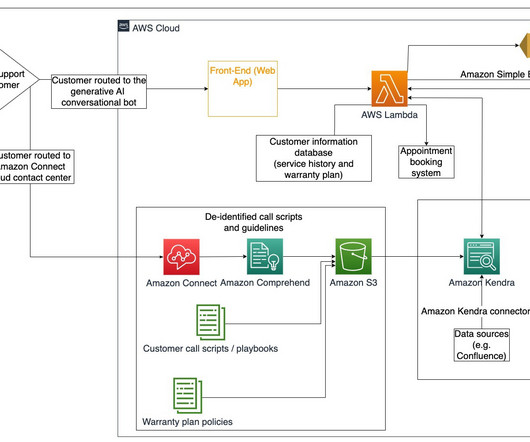
This data might have sensitive customer info, patient health records, or employee data. And if you want to apply a masking policy to a variant column, it’s a bit more complicated, especially with nested JSON data. Suppose we’ve applied masking policies to three fields: SSN, driving license, and date of birth columns.


















Let's personalize your content