Telegram combolists show that we are all hacked
Dataconomy
JUNE 4, 2024
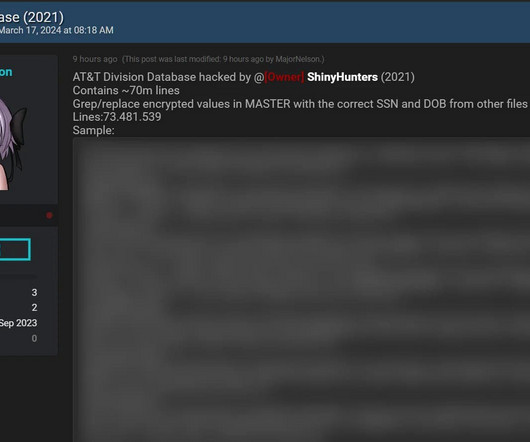
The leaked data typically consists of username and password combinations (often stolen via credential stuffing attacks or data breaches), usernames and passwords along with associated URLs (exfiltrated via password-stealing malware), and raw cookies (also stolen via password-stealing malware). . “It contained 1.7k


















Let's personalize your content