Cryptography use cases: From secure communication to data security
IBM Journey to AI blog
JANUARY 17, 2024
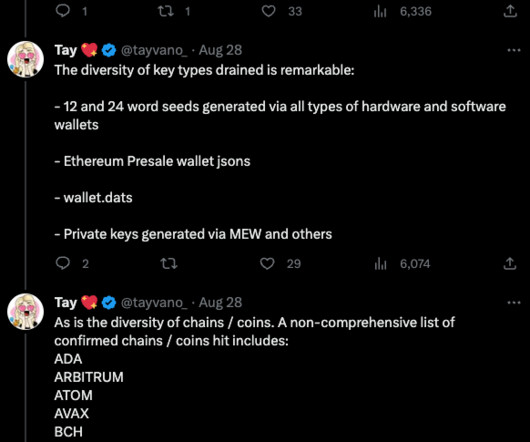
When it comes to data security , the ancient art of cryptography has become a critical cornerstone of today’s digital age. The main principles of cryptography establish trust when conducting business online. are kept secure. Key sizes, randomness and storage are all crucial functions of key management.





















Let's personalize your content