Algorithmiq Demonstrates Path to Quantum Utility with IBM
insideBIGDATA
JANUARY 13, 2024
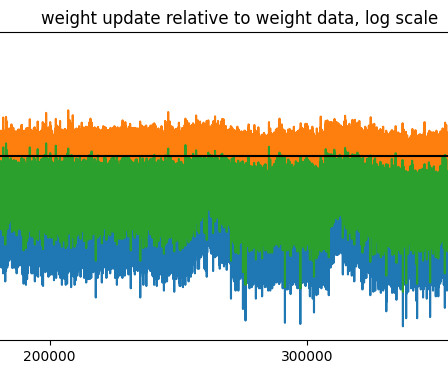
Algorithmiq, a scaleup developing quantum algorithms to solve the most complex problems in life sciences, has successfully run one of the largest scale error mitigation experiments to date on IBM’s hardware. This achievement positions them, with IBM, as front runners to reach quantum utility for real world use cases. The experiment was run with Algorithmiq’s proprietary error mitigation algorithms on the IBM Nazca, the 127 qubit Eagle processor, using 50 active qubits x 98 layers of CNOTS and th



































Let's personalize your content