The crucial role of data security management in the digital age
Dataconomy
JANUARY 10, 2024
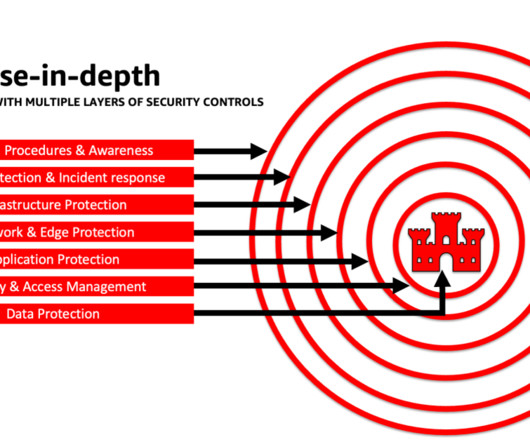
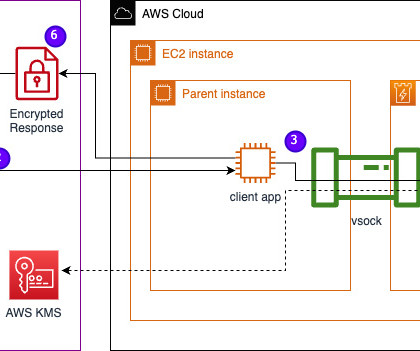
In today’s digital era, organizations heavily rely on data for their operations. However, given the increasing reliance on technology and the growing number of cyber threats, ensuring data security has become crucial. In this post, we will explore the role of managing data security in the landscape.












































Let's personalize your content