Project Clover: NCC takes the helm of TikTok’s data security
Dataconomy
SEPTEMBER 6, 2023
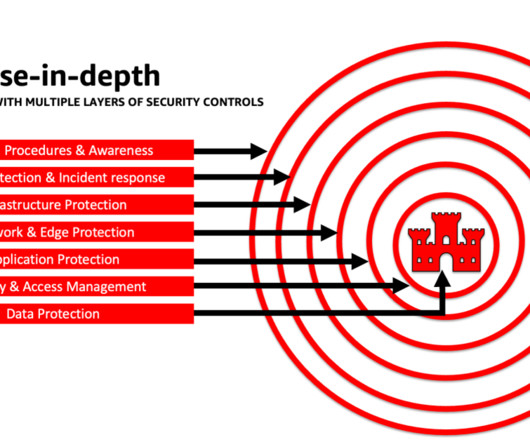
Core insight: Leveraging NCC Group’s cybersecurity expertise and certifications, TikTok is focusing on strengthening data controls and protections, including the inauguration of a Dublin data center and real-time security monitoring. NCC Group also operates as the managed security services provider for TikTok’s security gateways.


















Let's personalize your content