Getting Started with Cloud Security and its Applications
Analytics Vidhya
MARCH 2, 2023
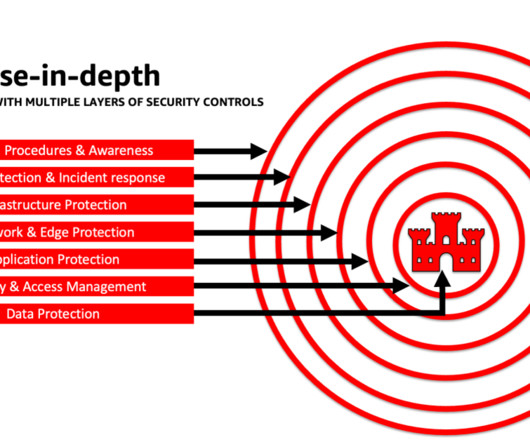
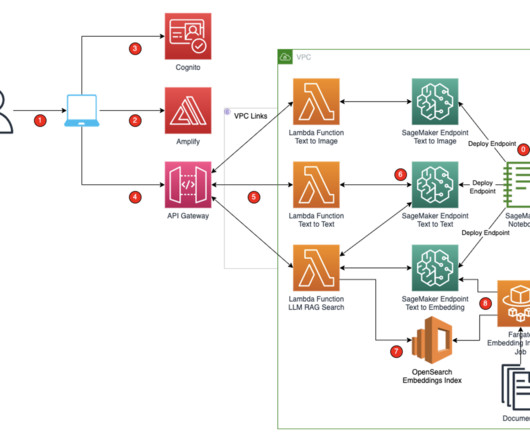
Introduction A guide to securing your data and applications will be presented throughout this article. Cybersecurity threatens cloud computing resources, including data, applications, and infrastructure. Most organizations store and process their data in the cloud.











































Let's personalize your content