Who’s Behind the Botnet-Based Service BHProxies?
Hacker News
FEBRUARY 24, 2023
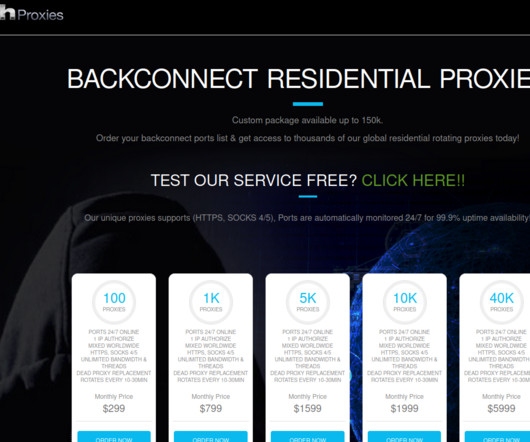
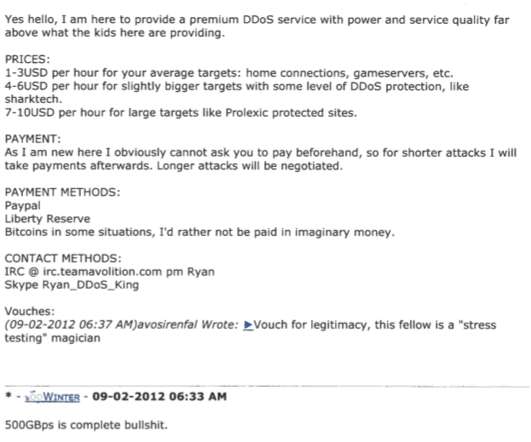
BHProxies has authored 129 posts on Black Hat World since 2012, and their last post on the forum was in December 2022. BHProxies initially was fairly active on Black Hat World between May and November 2012, after which it suddenly ceased all activity. The website BHProxies[.]com























Let's personalize your content