Inside the Massive Alleged AT&T Data Breach
Hacker News
MARCH 18, 2024
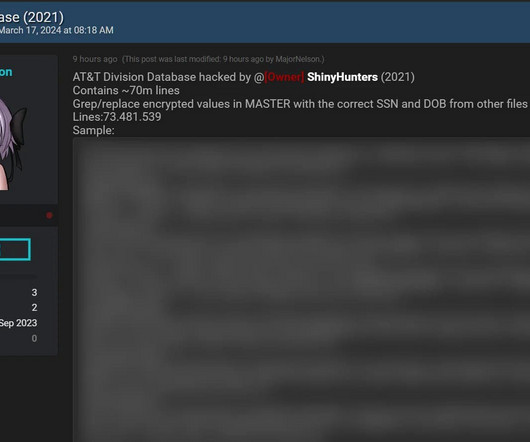
The Dropbox and LinkedIn breaches, for example, occurred in 2012 before being broadly distributed in 2016 and just like those incidents, the alleged AT&T data is now in very broad circulation. The file with decrypted SSNs has 43,989,217 lines and the decrypted dates of birth file only has 43,524 rows.



















Let's personalize your content